Data Security Learning Module
Digital Signatures
Created By Eng. Eslam Osama
Introduction to Digital Signatures
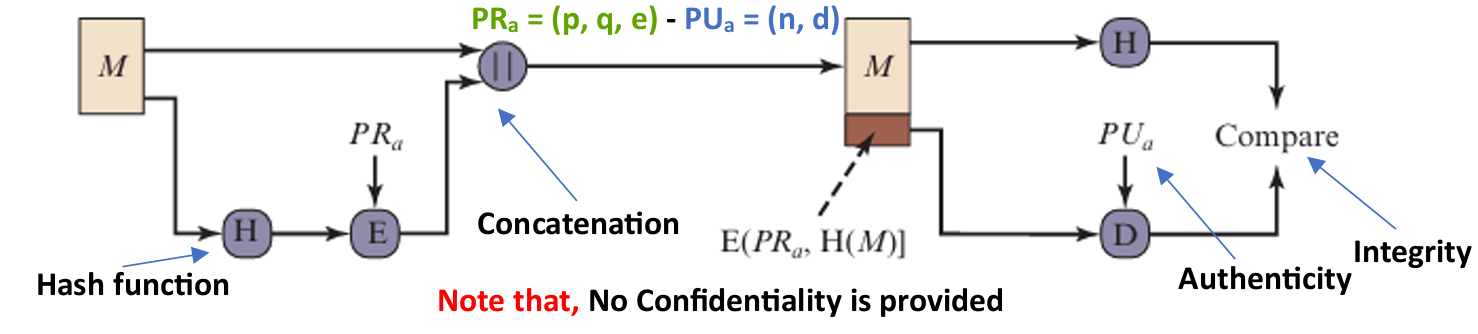
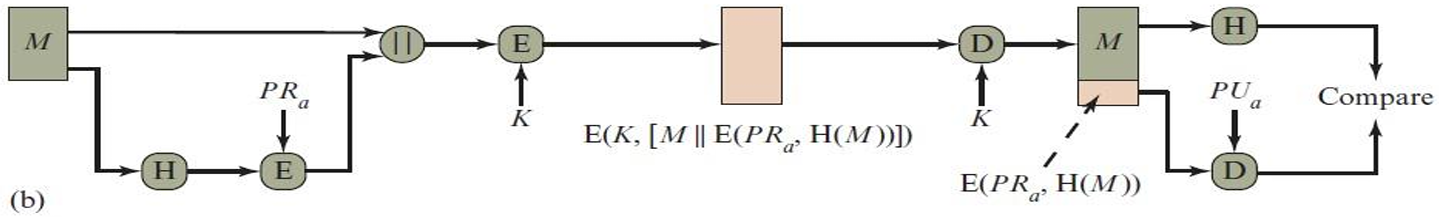
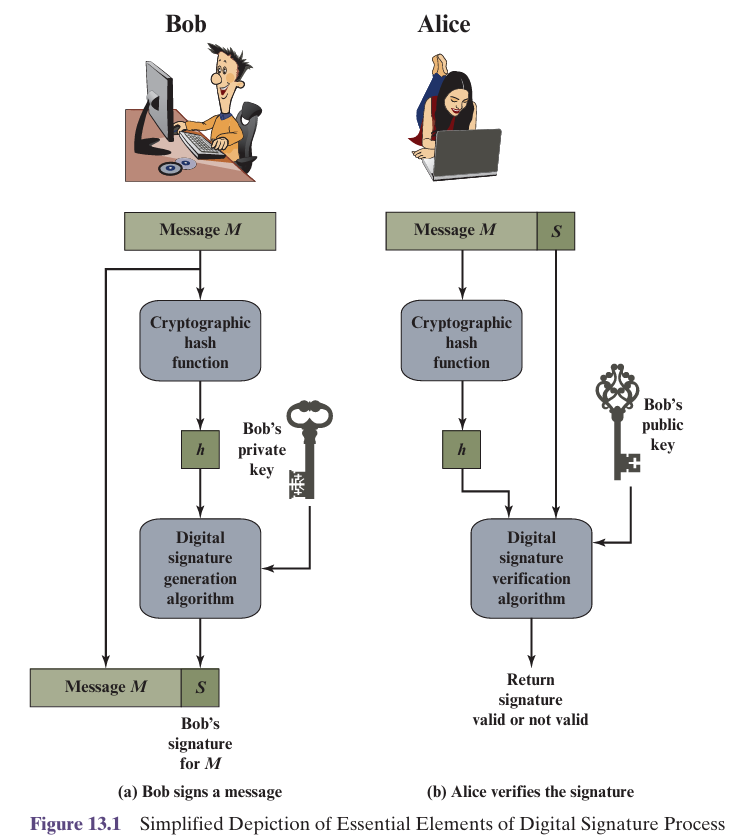
Digital Signature is a cryptographic technique that verifies the authenticity, integrity, and origin of a digital message or document. It is created using the sender's private key and verified using their public key.
Key Features of Digital Signatures
- Authenticity: Confirms the message is from the claimed sender (verified via public key).
- Integrity: Ensures the message hasn't been altered; any change breaks the signature.
- Non-repudiation: The sender cannot deny sending the message after signing it.
Important Notes:
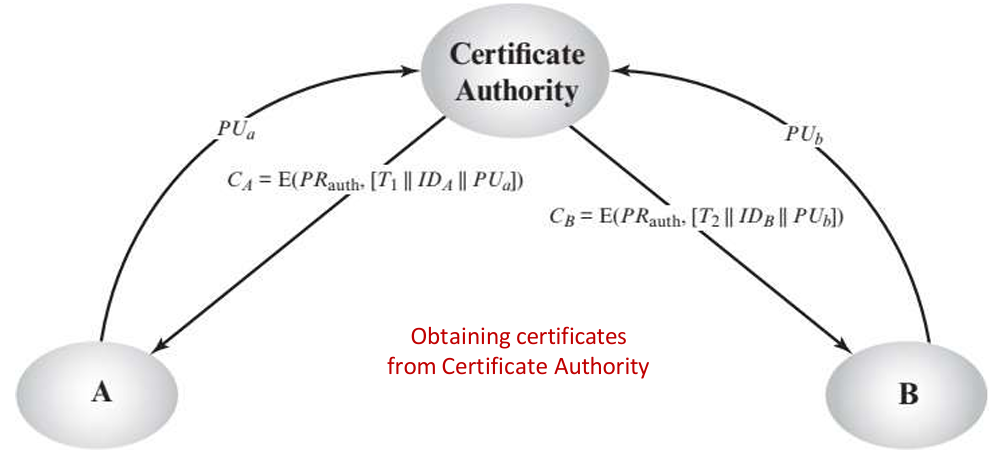
- Third-Party Authentication in Digital Signatures
A digital signature must be publicly verifiable, meaning a trusted third party can check its validity — not just the sender and receiver. This is often done using a Certificate Authority (CA). - Signatures Are Not Unconditionally Secure
Digital signatures are not 100% secure. An attacker might eventually break the algorithm, exploit weak random number generators, or use forgery attacks. Expiration dates help reduce this risk over time.